If you have an office, facility, or residence with a lot of guest traffic and are needing to provide the guests with their own network using your existing Meraki equipment, this is the best way to do it.
For this example the environment is using the following devices:
- Cisco Meraki MX100 Router
- Cisco Meraki MS350-48p Switches
- Cisco Meraki MR42 APs
Brief:
The Guest clients should:
- be denied access to the Secure network (LAN, Secure WLAN, etc)
- be unable to communicate with each other (client isolation).
- have bandwidth restrictions.
- have unique content filtering policies
Under this model, you will have the most flexible, easiest possible Guest Network to manage.
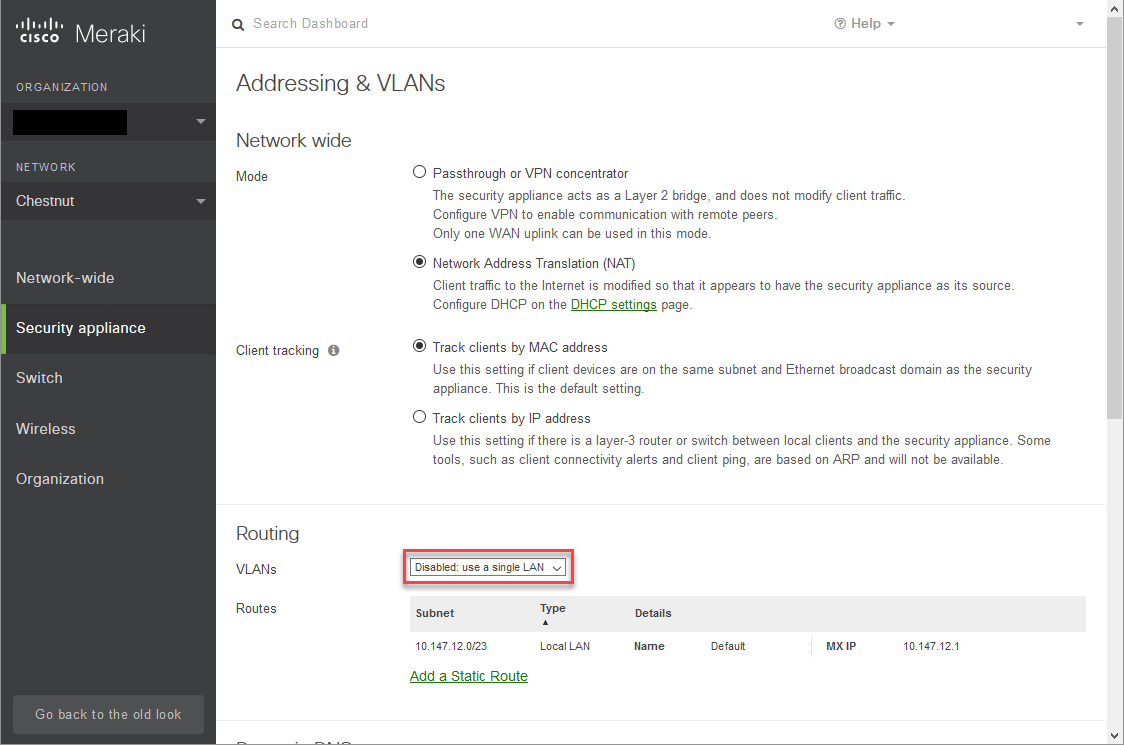
Creating the VLAN on Meraki MX.
- Enable VLANs if not already
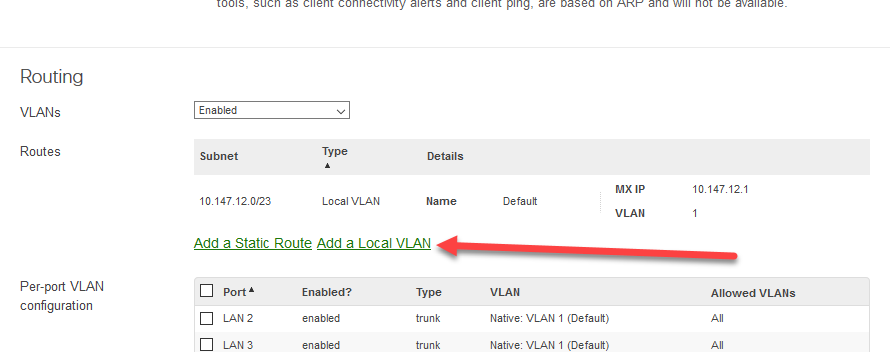
- Drop down VLANs and select “Enabled”
- Click Add a Local VLAN
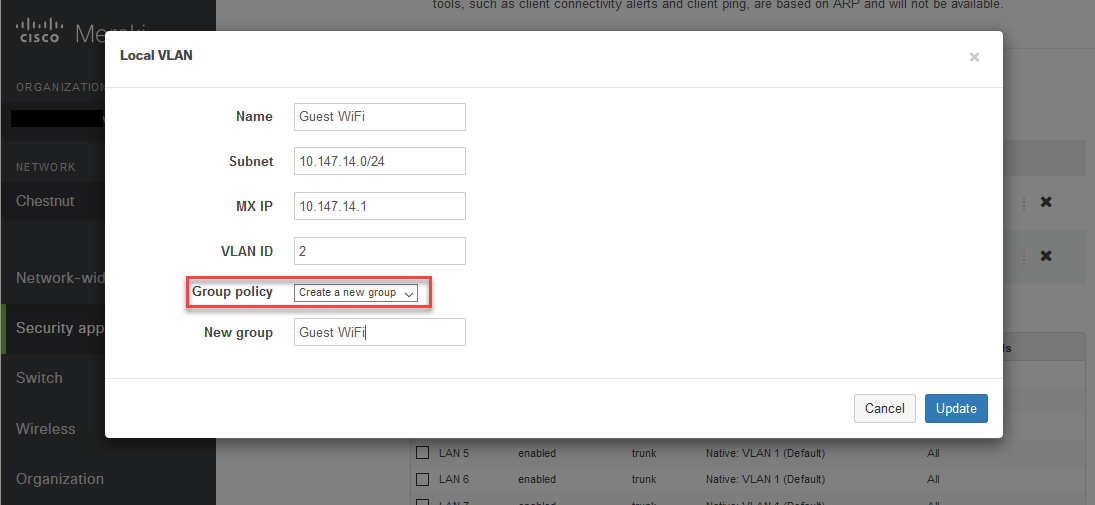
Here you will choose an IP subnet for the Guest Network. I will not be going over any details of IP subnetting.
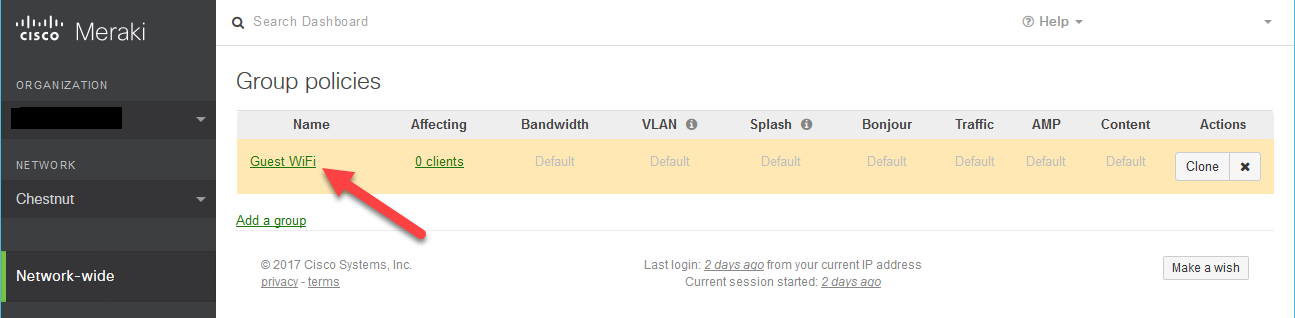
- While making the VLAN, also make a new Group and name it accordingly (Guest, Guest WiFi, etc)
- (We will use this later)
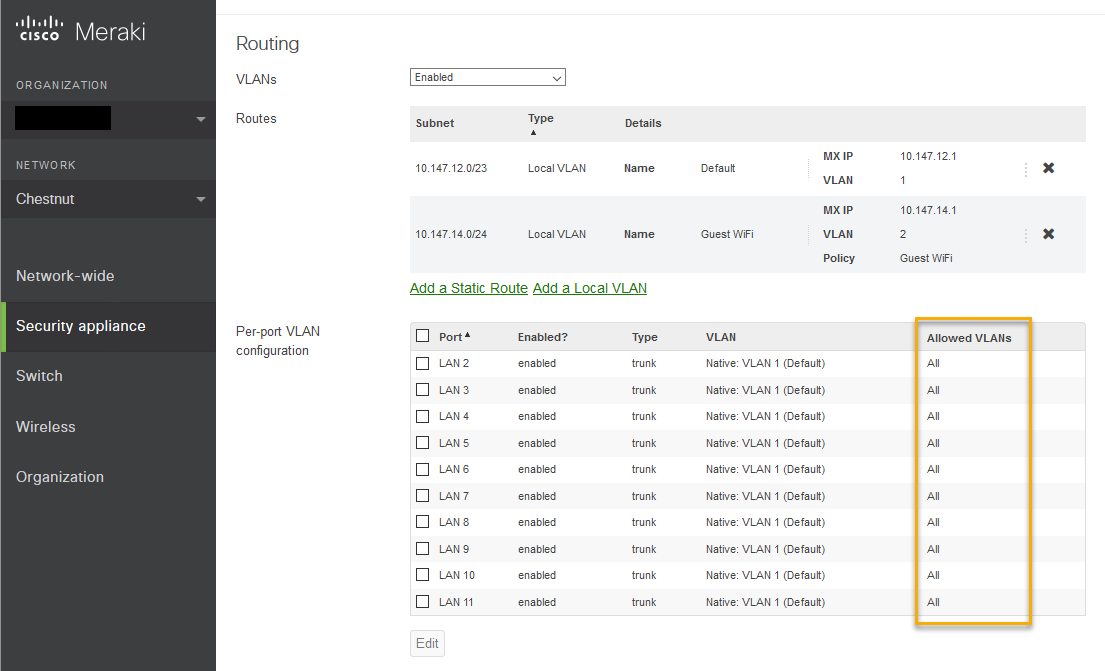
Interfacing with the VLAN
Right now all VLANs are allowed on all of the interfaces.
- This is fine for the purposes of this guide, but tagging the ports specifically will make for a more secure network. I will not cover this for the purposes of this guide.
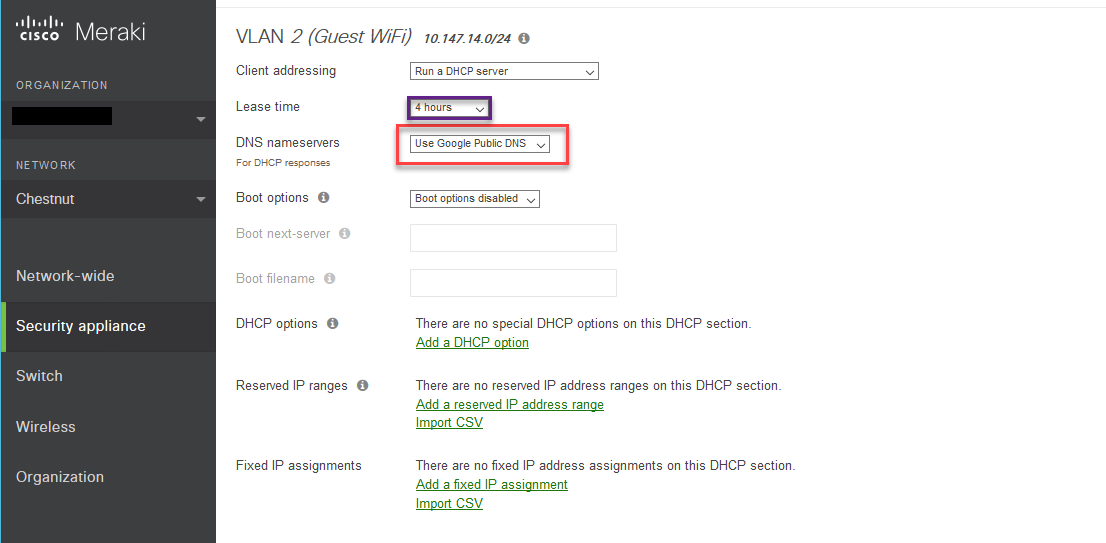
DHCP for the Guest Network
The VLANs scope has been given a DHCP server automatically. Before your guests connect to it, it’s best that you push them good settings the first time so they don’t have to wait for lease to expire to get the proper DHCP options.
This is what I decided to do for the Guest SSID DHCP:
- Set lease time to 1 or 4+ hours, depending on traffic of the building.
- Set DNS Nameservers to publicly accessible servers (google, opendns)
- you don’t want your clients using your Secure Network’s DNS. In fact, you will probably be forbidding that in the firewall later in this guide.
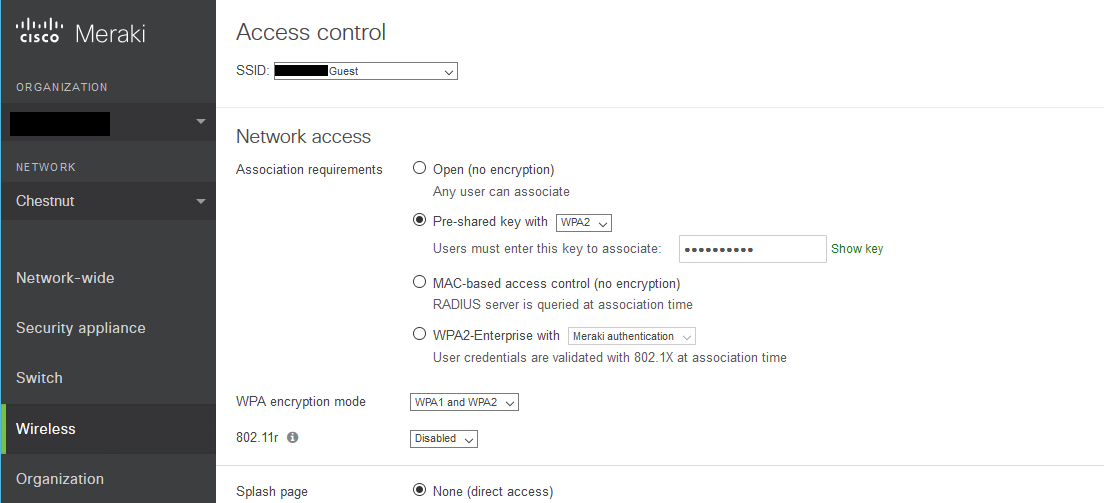
Configure your Guest SSID
I’m in the Access Control portion of the Wireless configuration, and I have the Guest SSID selected.
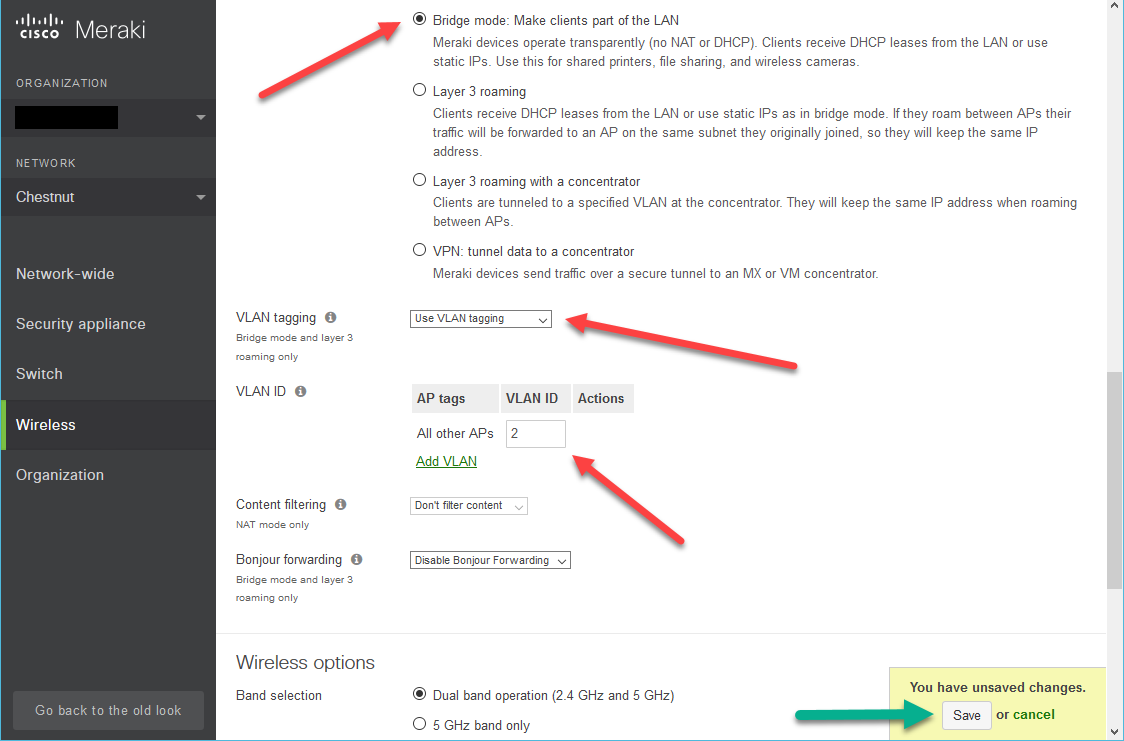
- You must enable Bridge Mode for this SSID
- Then you can select from dropdown “Use VLAN tagging”
- Specify VLAN 2 (or whatever you used for your Guest VLAN)
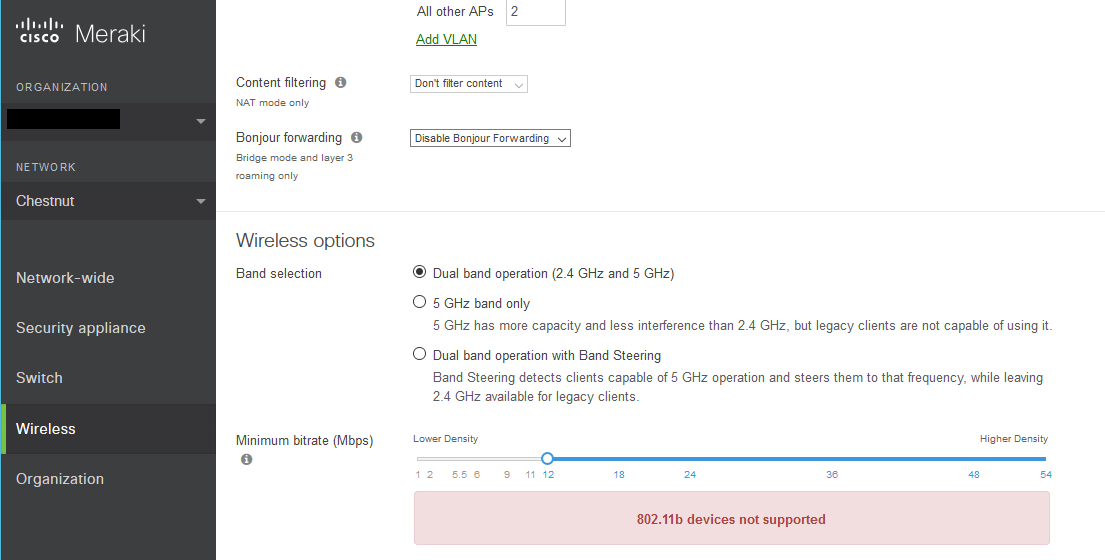
If you want to increase performance of your network, you can kick off the 802.11b clients like below.
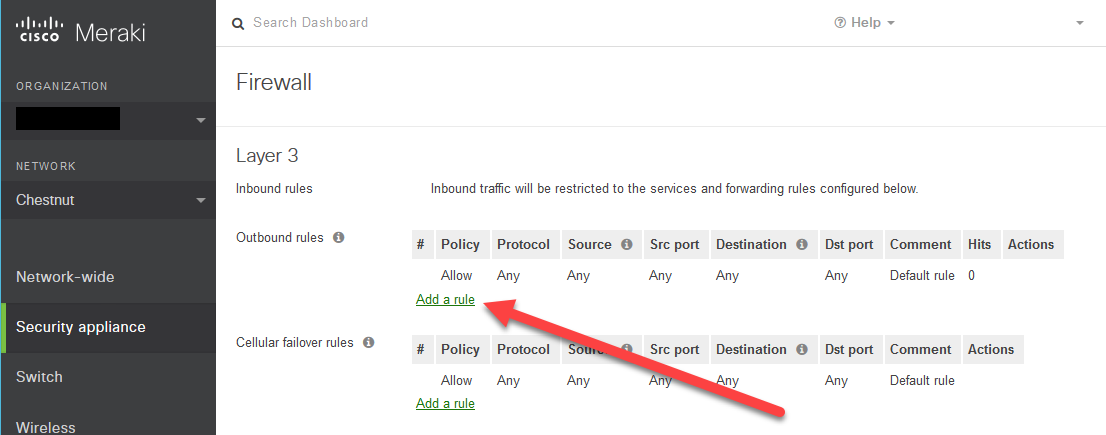
Firewall Rules
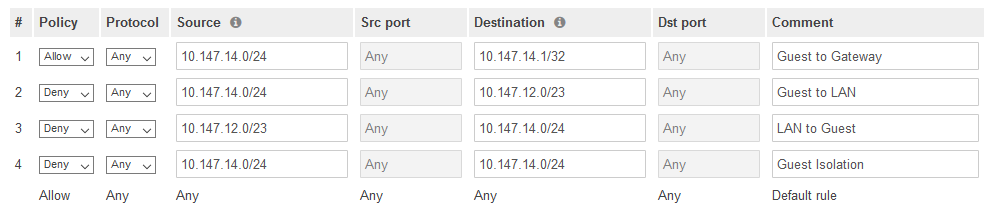
In case it hasn’t been clear, my subnets for this example are:
Secure: 10.147.12.0/23
Guest: 10.147.14.0/24
- I’ll be using these subnets to craft rules for how they can live together on the same equipment yet be isolated.
We’ll need to deny these flows:
- Guest –> LAN
- LAN –> Guest
- Guest –> Guest (Client Isolation)
But it’s imperative that we allow this as the first rule:
- Guest network –> Gateway
This is because of the guest client isolation. It would prohibit them from reaching out to the internet if they couldn’t reach 10.147.14.1
- Here are the firewall rules I used to make this happen:
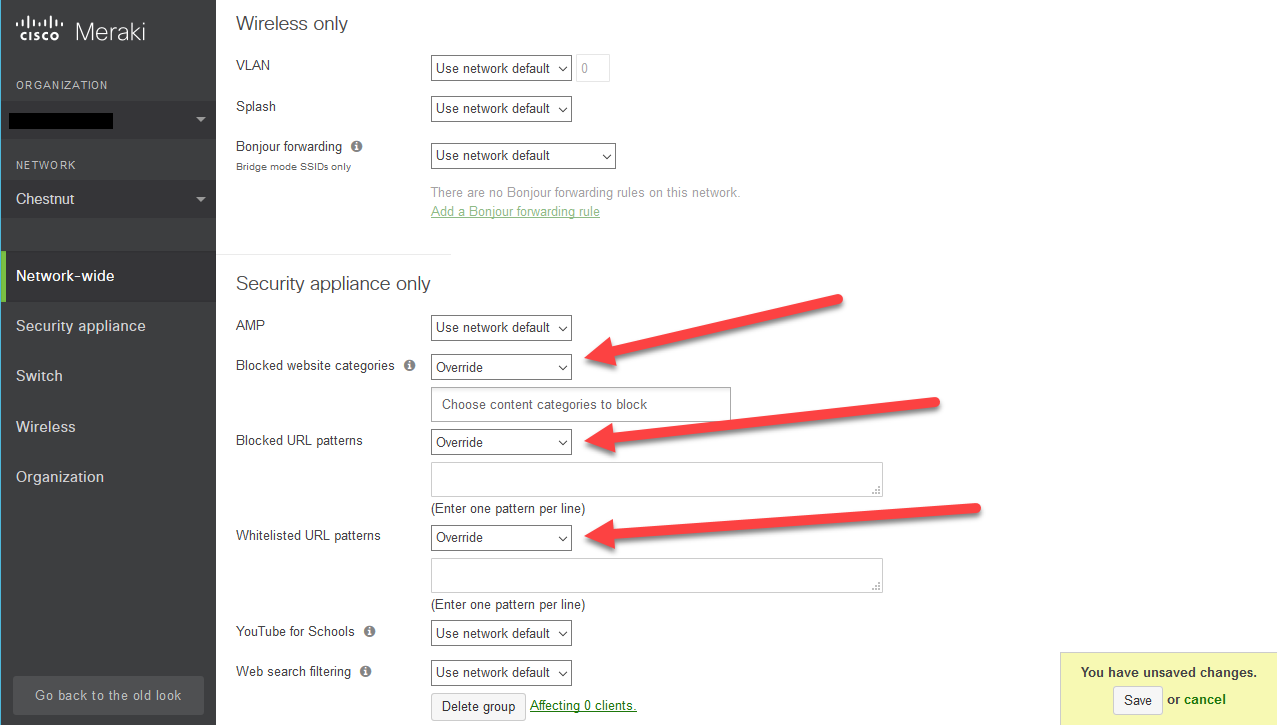
Group Policy configuration
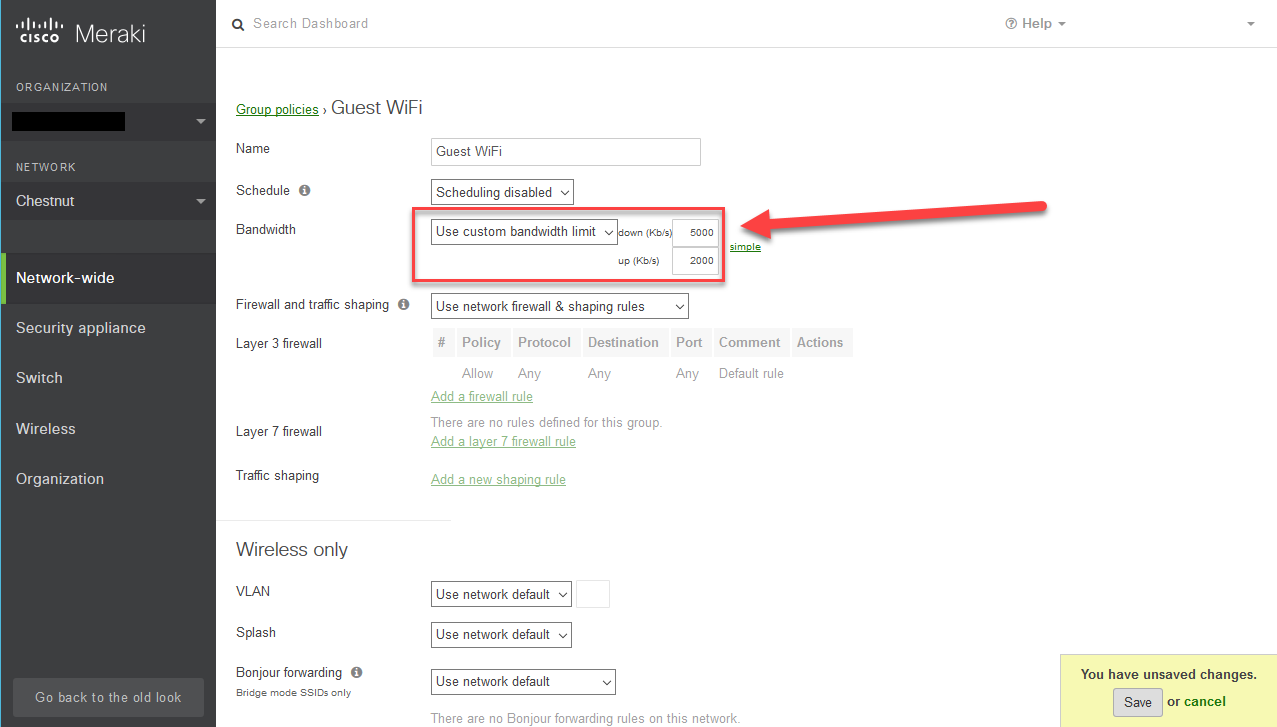
The Meraki Group policy allows you to do a lot. Here we’re using the Guest WiFi Group Policy I made when I set up the VLAN earlier in the guide:
- I’m going to use this policy to impose the following restrictions on guests:
DL Speed – 5 Mbps
UL Speed – 2 Mbps
Block Websites by category
Block specific URLs
Whitelist specific URLs
You can do more if you choose to.
Bandwidth throttling:
Content filtering:
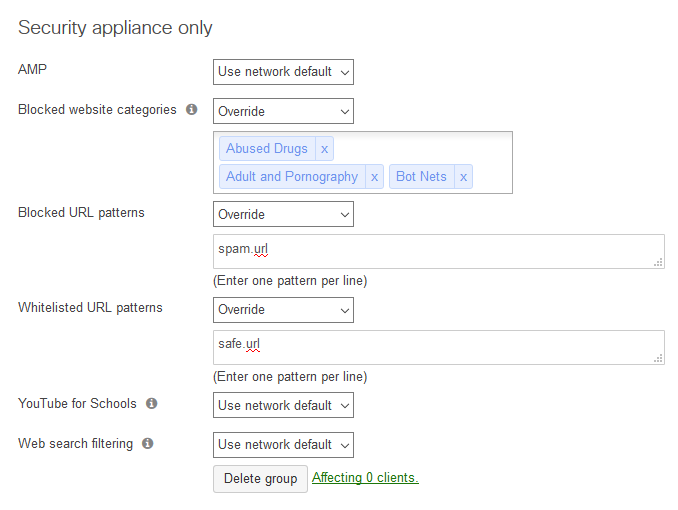
- Choose override for each entry you would like to specify.
- For example:
Finished.
Now, anyone who connects to your Guest WiFi SSID will be on an secure/isolated network with whichever specifications you’ve chosen.
Feel free to leave any comments or feedback and also drop a note if you are using this method and have anything you would like to share!

1 Comment
賓果賓果開獎程式 · September 25, 2017 at 5:18 am
賓果賓果開獎程式
Excellent blog here! Also your site loads up fast! What host are you using? Can I get your affiliate link to your host? I wish my site loaded up as quickly as yours lol